
Everyone has heard of Meltdown and Spectre vulnerabilities in modern computers, leaking passwords and sensitive data. In case you don’t, the most important thing to remember is to update all devices with an Intel processor, including mobile devices. If you are using Microsoft Intune to manage mobile devices in your organization, you can configure compliant rules to force the users to update their operating system version.
Those who want to keep their old OS version will lose access to Office 365 at one point. Employees must know the importance of updating their devices more often without being enforced. On the other hand, updating OS means some types of the device won’t be supported anymore. If your company accepts BYOD, some users must purchase a new mobile device. In the end, securing your endpoints is more critical.
In this post, we will use the Meltdown and Specter vulnerabilities with the iOS platform. The iOS version that resolves Meltdown and Specter vulnerabilities is 11.2.5 to further protect against Spectre exploits. Note that this guide can be helpful for future breaches, other supported platforms, and the new versions.
Intune App Protection (Warning)
There are two ways to enforce a minimum iOS version: the first is enabling a warning message on each connectivity to an app and giving the users a grace period to update their devices, or the second, quite simply blocking access to Office 365 right away.
Intune App Protection allows IT to send a warning message to the devices and keep access to company data. This popup will appear each time users connect to a company app, like Outlook. This technique slightly eases productivity and doesn’t affect user experience. At this stage, it’s not mandatory to be enrolled in Intune.
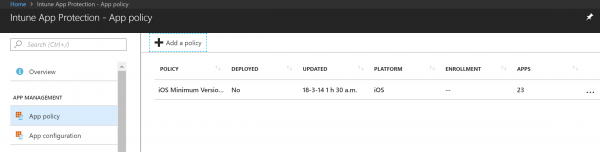
- Open https://portal.azure.com with your browser, and click on the node Intune App Protection – App Policy
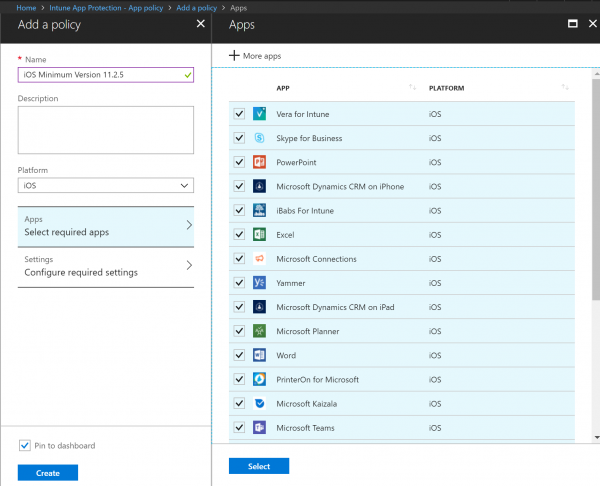
- Click on Add a policy and enter the name of the policy iOS Minimum Version 11.2.5
- iOS
- Select Apps blade and select all applications from the list
- Once you finish, click on Select
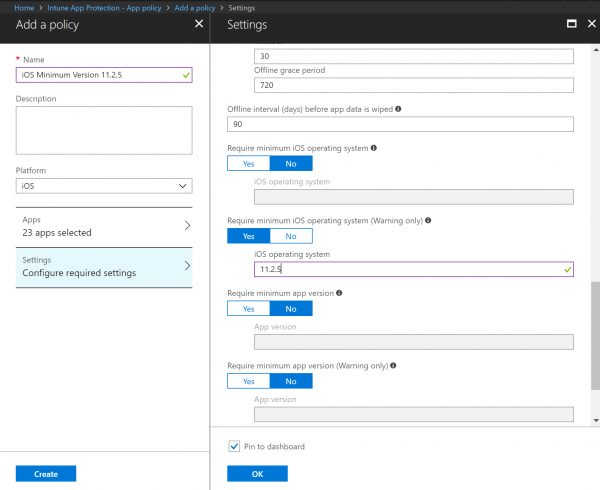
- Click on Settings blade and scroll down in the right section till you see Require minimum iOS operating system (Warning Only)
- Select Yes and enter the version you want to enforce. In our example, is 11.2.5
- Click OK and select Pin to Dashboard if you want to see the statistics of this policy in your Azure Dashboard.
The policy is completed; it’s time to deploy it to an AAD group.
- Select the policy you just created.
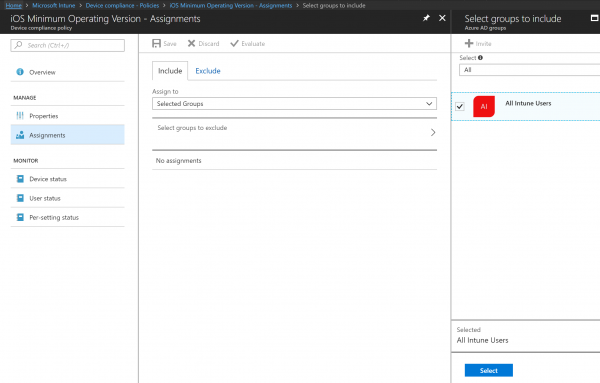
- In the Assignments node, you include the group of people you want to target
- Make sure you are on the Include tab and select groups to include
Tips: Test your policy with colleagues before deploying at large.
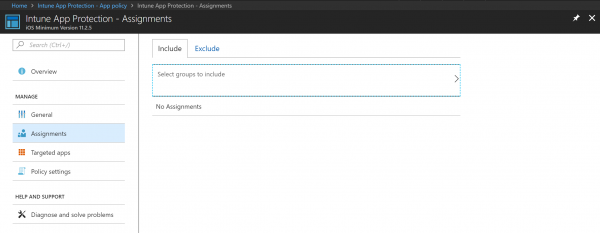
- Find the AAD group you want to target and click Select
Under those circumstances, expect the users to get this kind of warning message if they are not compliant. It won’t affect access, and the user can continue working by clicking Ok.
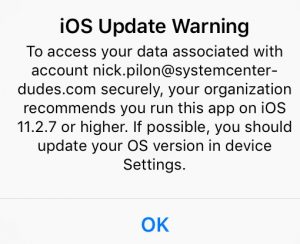
The good thing about sending a message to a user’s device is they are not losing productivity and can upgrade their devices with personal wifi during off-hours. The sad thing is the breach is still there. You can give a few days (3-7) grace period, and once it’s over, kill the switch.
Intune App Protection (Block)
To block access to mainly Office 365 apps, you can still use Intune App Protection. At this stage, it’s not mandatory to be enrolled in Intune.
- Return to the Policy Settings blade of your policy and disable the warning message.
- Enable Require minimum iOS operating system and enter 11.2.5
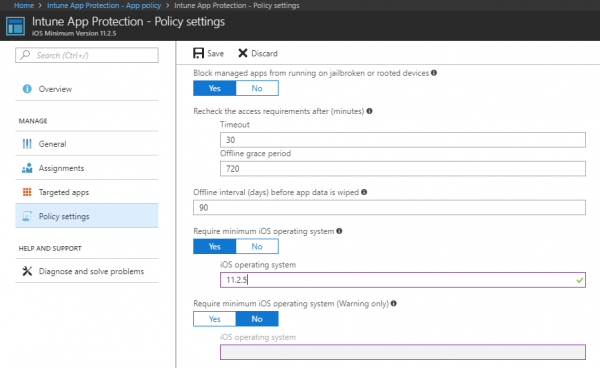
If the user still has not updated their mobile device, their access will be blocked, and this message will be displayed.
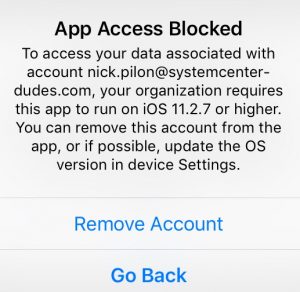
There are only 2 options: Remove Account or Go Back.
Compliance Policy State with Conditional Access (Block)
Unfortunately, the next step is protecting access to your company’s data using Conditional Access. Business data is precious nowadays, and breaches are expensive for businesses. That’s why it’s essential to ensure your mobile devices comply with security policies.
With Microsoft Intune, you can configure a device compliance policy that enforces a required minimum operating system version. Assign that policy to users by using AAD groups. Overall, using conditional access is more efficient than only Intune App Protection.
- To configure a compliance policy, navigate to https://portal.azure.com, then click on Intune Blade and Device Compliance
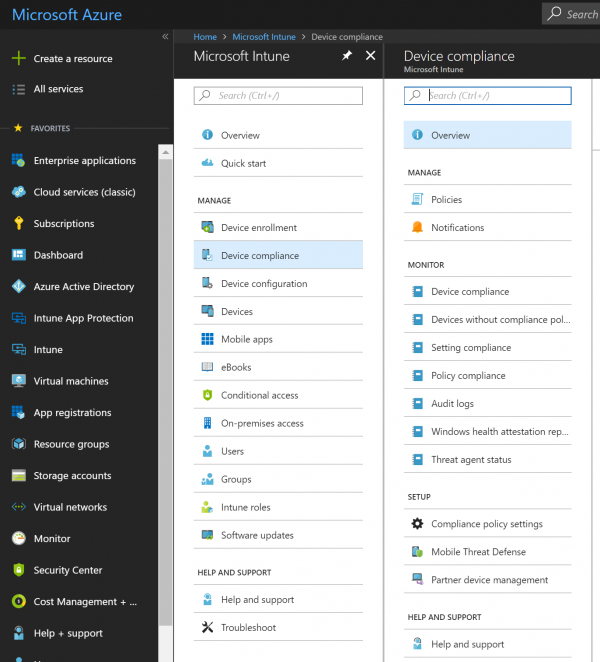
- Click on Policies and Create Policy
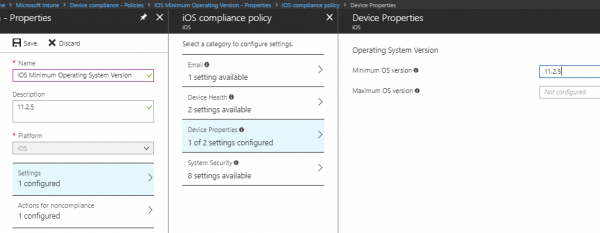
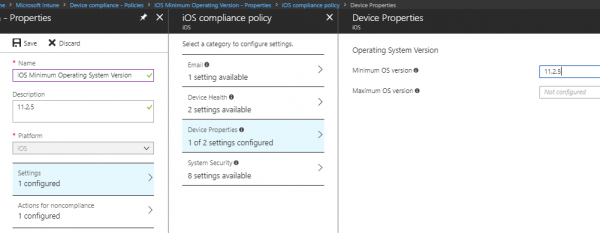
- You will arrive at the Create Policy properties and enter a policy name like iOS Minimum Operating System Version.
- You can add a description of your policy; it’s not a mandatory field
- Choose the Platform, in our case, is iOS
- Click on Settings – Device Properties, and in the Minimum OS version field, enter the version you want to enforce 11.2.5
- Select OK, OK and Create
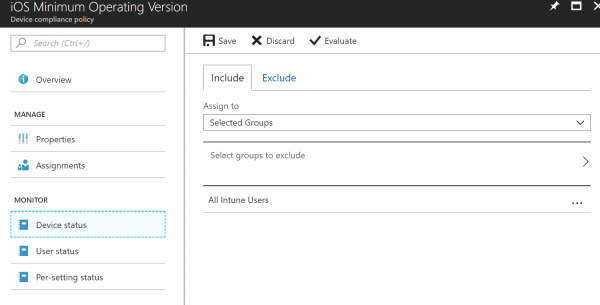
- Once the policy is created, click Assignments Blade to deploy the policy to users.
- For the Assignment properties, click on Select groups to include, select your specific group and click Select to confirm
- You can also select the option All Users by clicking on Selected Groups
- In conclusion, you click Save when you’ve finished with the assignment
Tips: Test your policy with colleagues before deploying at large.
The configuration of the device compliance policy is completed and assigned to users. We are now ready to configure conditional access to ensure all users trying to access company data from non-compliant devices will be blocked.
- Click on the Conditional Access in the Microsoft Intune blade or from the Azure Active Directory blade, and select Policies and New Policy to create a new conditional access policy.
- The first thing you need to do is give a name to your policy
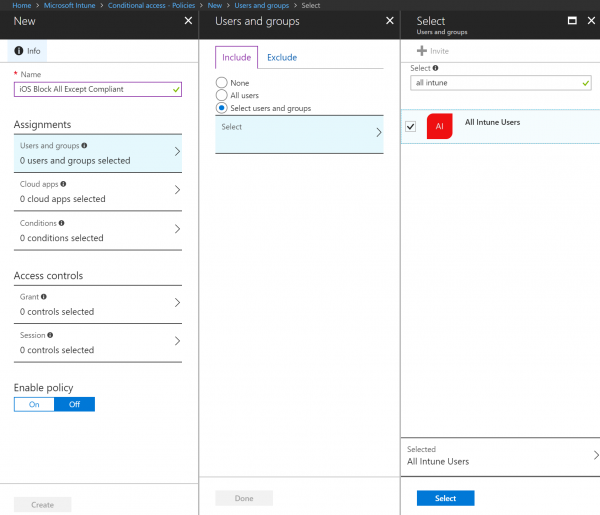
- From the Assignments section, click on Users and Groups and select your specific groups or All users
- Once it’s completed, click on Select and Done
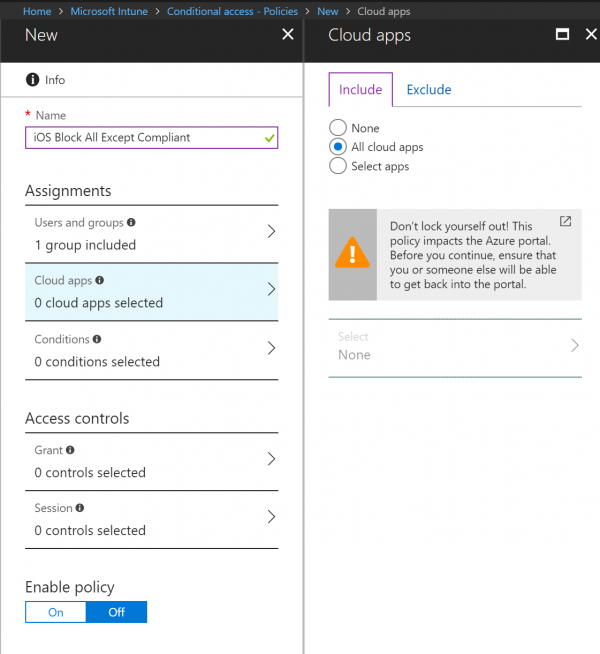
- In the Assignments section, click on Cloud Apps and select All Cloud Apps or a specific app.
- Click Done
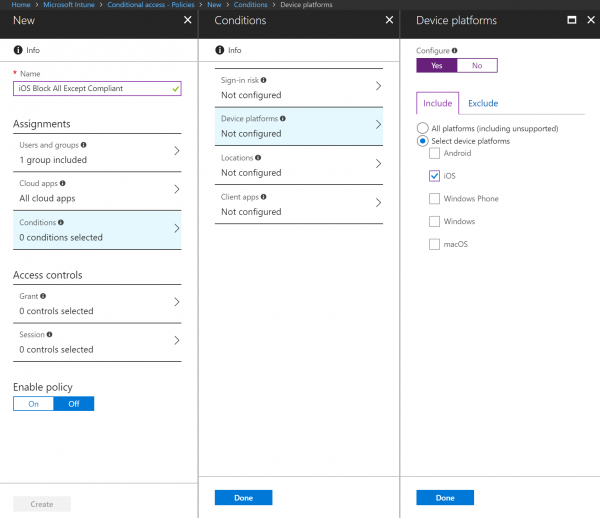
- Still, in the Assignments section, click on Conditions Blade and Device Platforms.
- Enable the settings by clicking on Yes just beside Configure
- In the Include tab, select iOS
- Click Done and Done
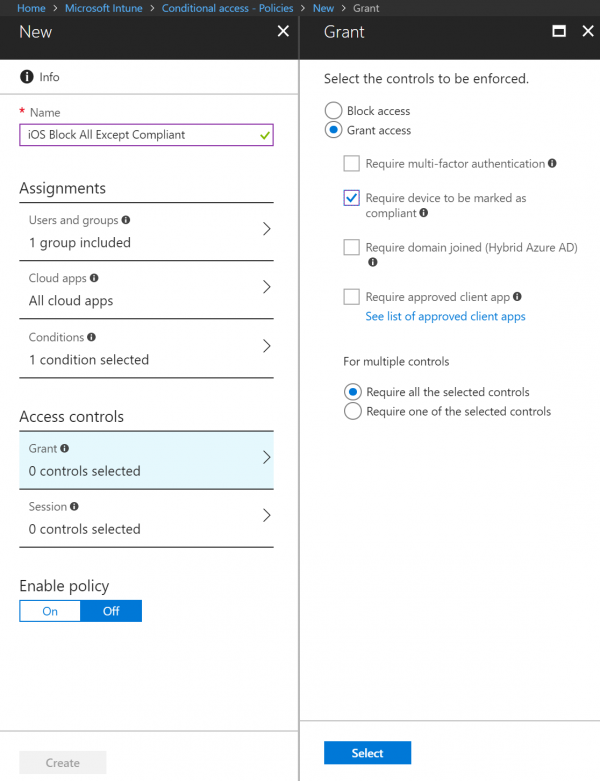
- In the Access Controls section, click on the Grant blade
- Select the Grant access option and click the checkbox Require device to be marked as compliant
- Click Select
- Enable the policy and click on Create
The End Result
Now that the conditional access rule and device compliance are configured, users will begin to receive this kind of message once they start to authenticate to some applications from their mobile devices.
Not Enrolled in Intune
You will get this message if your mobile device is not enrolled in Intune.
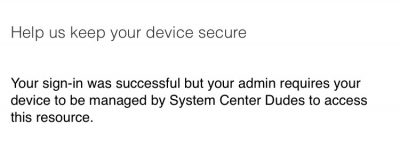
Click on Enroll and follow the steps to enroll the device in Intune.
Not Compliant
You will get this message if your mobile device is enrolled in Intune but not compliant.
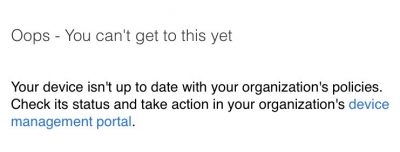
An excellent way to see why your device is not compliant is to open the Company Portal app and do a compliance check.
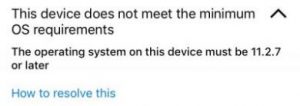
At this point, your only option is to update your operating system before thinking of connecting to the company apps.
If you want to monitor Spectre and Meltdown vulnerability on workstations using SCCM, you can take a look at this post.
Good luck!











Only authorized users can leave comments
Log In