
You may manage BitLocker in your organization using SCCM (MBAM). It’s also possible to create a policy for Bitlocker if you’ve switched to modern management and Endpoint Manager (Intune).
If you’re not aware, Bitlocker is a Microsoft solution for drive encryption. Bitlocker is not a new solution. It has been introduced in Windows 7. As a system administrator, you can manage how to deploy it, its policy and the most important part, keeping the recovery key in a safe place.
BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later. The TPM is a hardware component installed in many newer computers by computer manufacturers.
In this post, we’ll show you how to create your first Intune Bitlocker policy (Endpoint Manager) for your Windows 10 computer. We’ll also give you some troubleshooting tips and tips on managing it in the long term.
Bitlocker Policy Intune Requirements
In Microsoft Intune, there’s no specific requirement to create a Bitlocker policy except that you need the right permission.
However, if you’re unfamiliar with Bitlocker, there’s some requirement on the OS side. We recommend that you use a computer equipped with a TPM chip.
You can use the Endpoint Security Manager Built-in Role or create a new role and use the Remote Tasks permissions, including Bitlocker actions.
To use the Endpoint Security Manager role :
- In the Endpoint Manager Console
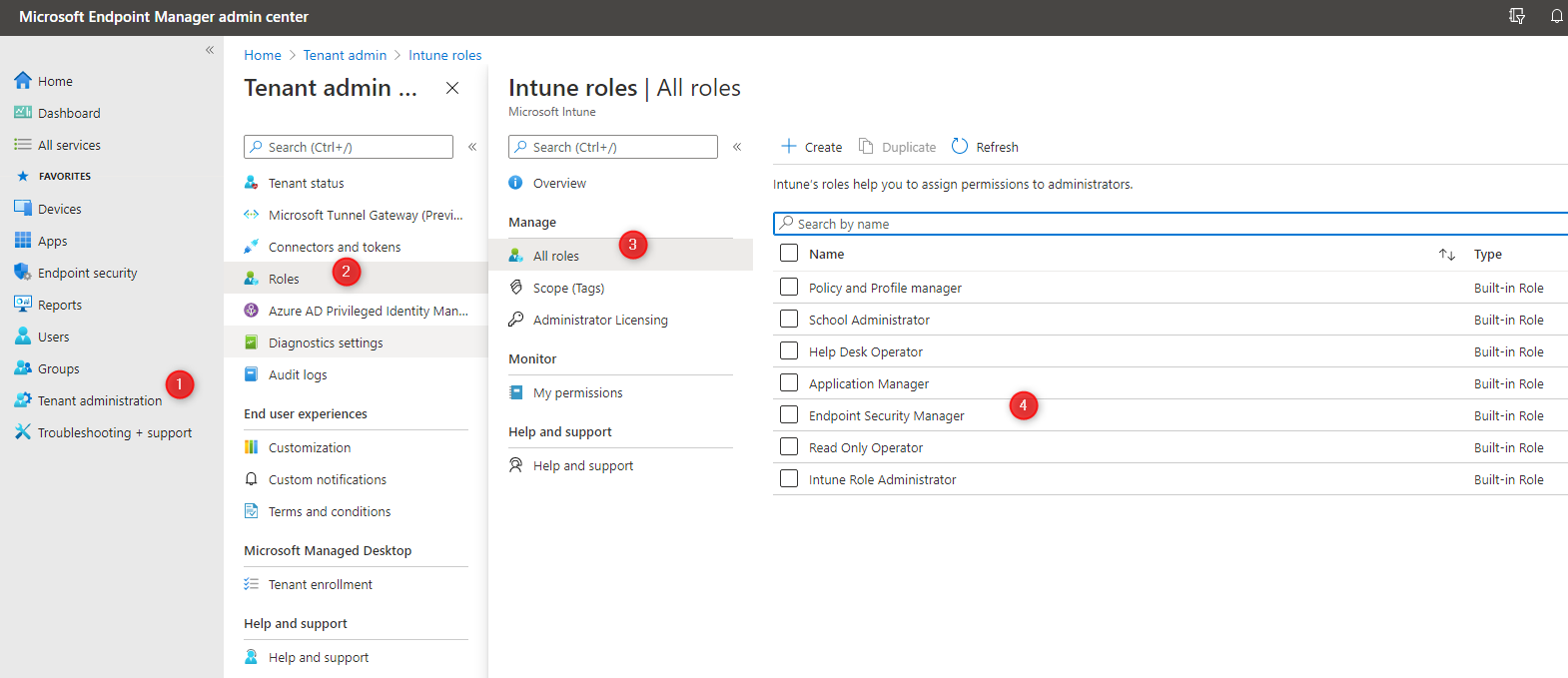
- Go to Tenant Administration / Roles / All Roles
- Add your user to the Endpoint Security Manager
To use a new group :
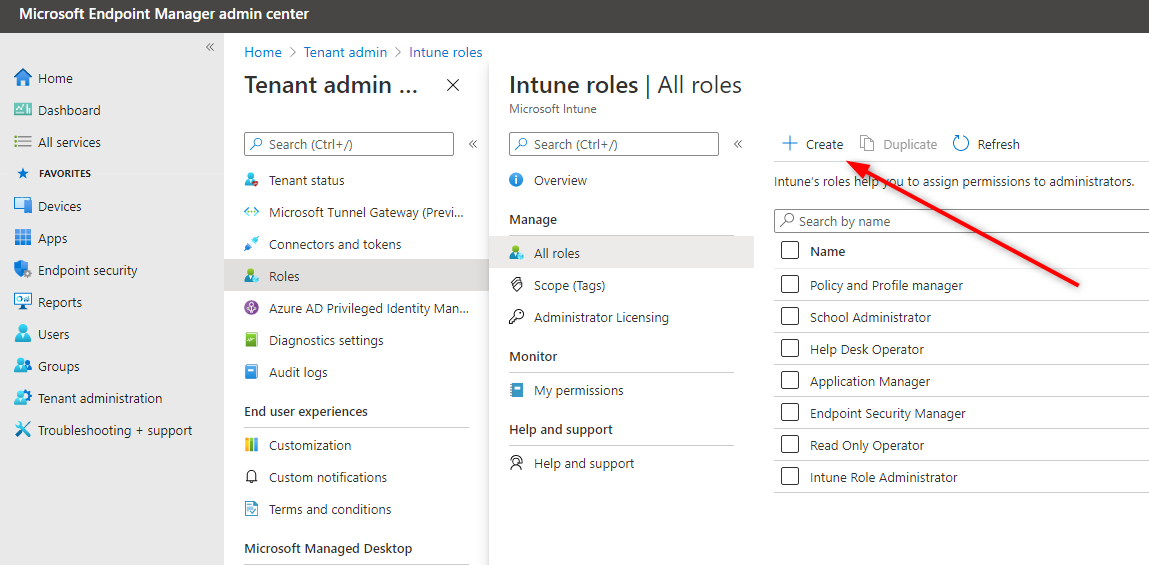
- In the Endpoint Manager Console, go to Tenant Administration / Roles / All Roles / New Role
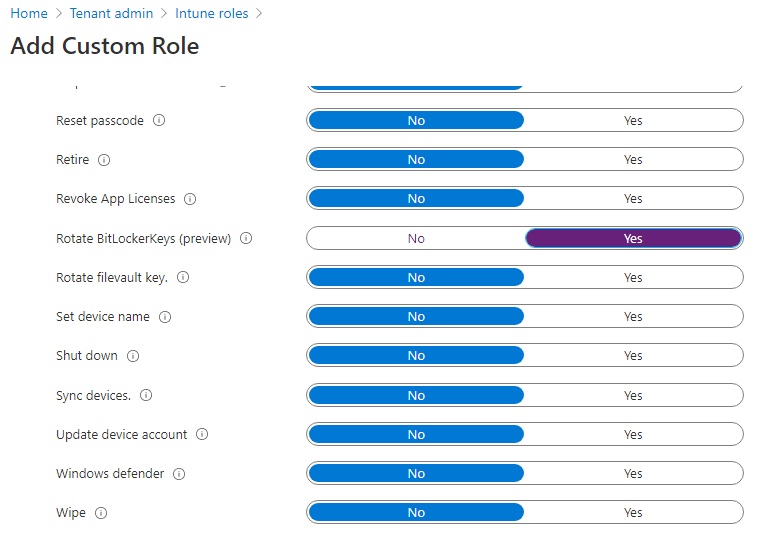
- Create a new group and select the Rotate Bitlocker Key action under Remote Tasks to your newly created group
Create the Bitlocker Policy in Intune
It’s now time to create our first Bitlocker policy.
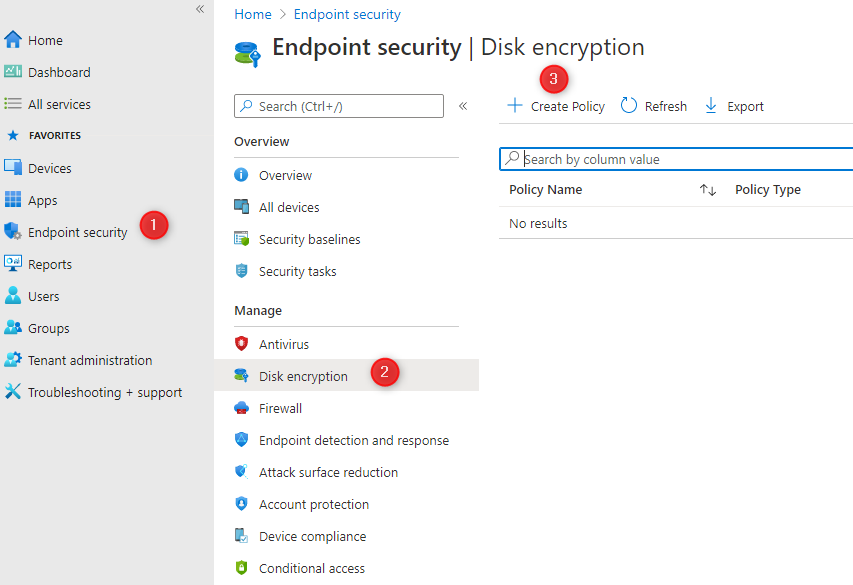
- In the Endpoint Manager Console, go to Endpoint security / Disk encryption / Create Policy
- Under Platform, select Windows 10
- Under Profile, select BitLocker
- Click Create at the bottom
- On the Basic tab, enter a policy name and click Next
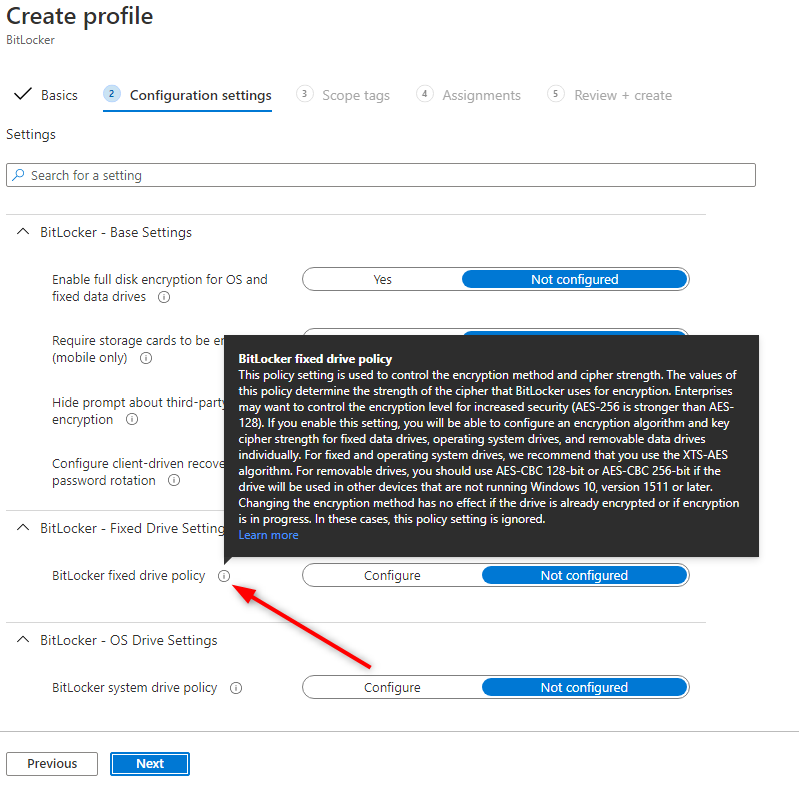
- In the Configuration Settings pane, enter the desired options. There’s a lot of available options, but Microsoft has done a great job explaining it using the little “i” symbol. Just hover over a specific setting to have an explanation.
Silently enabled Bitlocker on the devices
Suppose you need to install your policy without user intervention silently. You must set the following options in your configuration settings:
- Warning for other disk encryption set to Block
- Allow standard users to enable encryption during Azure AD Join set to Allow
- Compatible TPM startup PIN must not be set to Require startup PIN with TPM
- Compatible TPM startup key must not set to Require startup key with TPM
- Compatible TPM startup key and PIN must not set to Require startup key and PIN with TPM
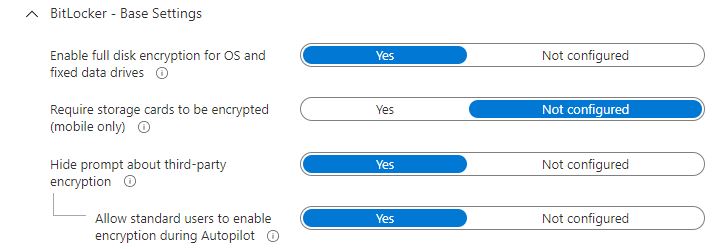
During the configuration settings section, make sure to configure Base Settings like below:
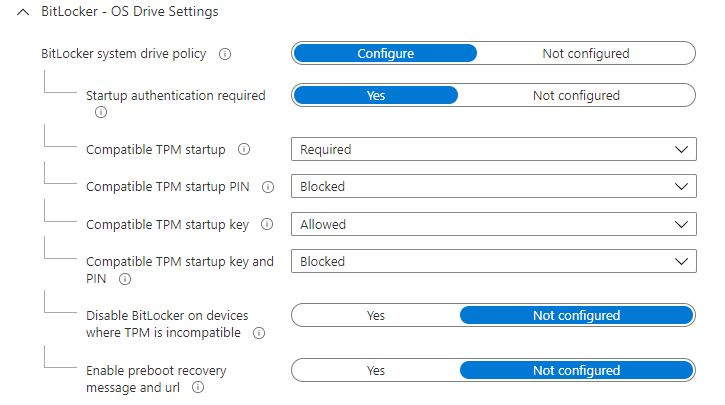
In the OS Drive Settings, configure the section like below:
In addition, Microsoft documentation state that the device must meet the following requirements for silent installation:
- If end users log in to the devices as Administrators, they must run Windows 10 version 1803 or later.
- If end users log in to the devices as Standard Users, they must run Windows 10 version 1809 or later.
- The device must be Azure AD Joined
- The device must contain TPM (Trusted Platform Module) 2.0
- The BIOS mode must be set to Native UEFI only.
Deploying the Bitlocker policy to an AAD Group
- So once your options are set, click Next
- In the Scope Tags tabs, enter scope tags if needed, click Next
- In the Assignment tab, choose the group of device you want to deploy your configuration, click Next
- Review your options and click Create at the bottom
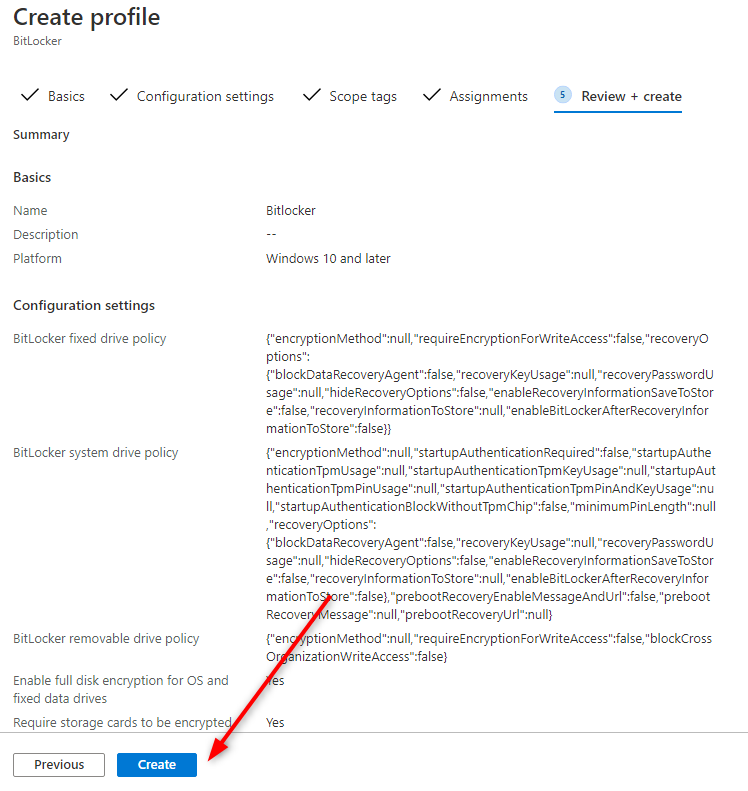
- Back in the Disk Encryption node, validate that your Policy has been created
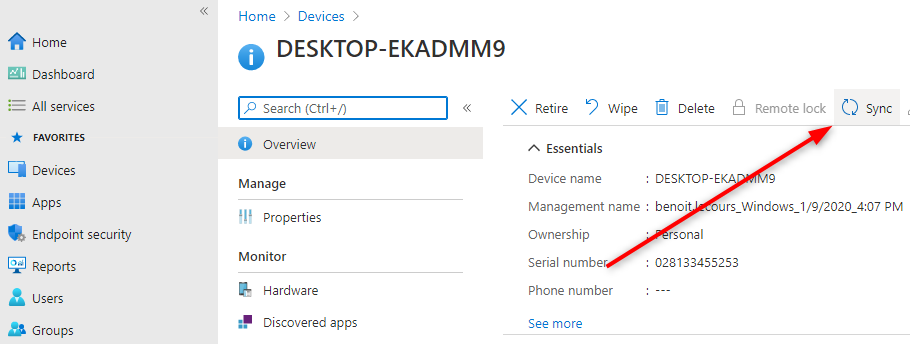
You can now log on a machine or use the portal to initiate a Sync request for your machine to receive the new policy.
- Go to Devices / All Devices and click on your Device
- On the top, click the Sync button
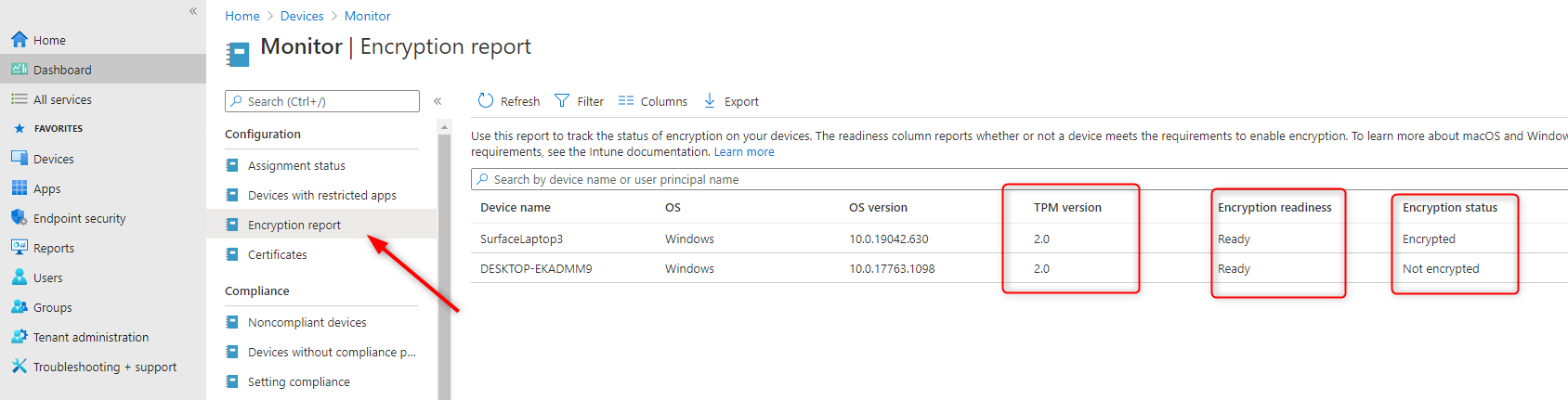
Monitor your Bitlocker Deployment
It’s now time to see if our policy is working. To monitor your Bitlocker deployment :
- Go to Device / Monitor / Encryption Report
- All required information is displayed
- In our example, the DESKTOP-EKADMM9 machine is not yet encrypted
Troubleshooting Intune Bitlocker Policy
Suppose you encounter an error while encrypting a device. The first step is to look at the Event Viewer of the affected machine.
Bitlocker events are stored in Applications and Services logs\Microsoft\Windows\BitLocker-API and BitLocker-DrivePreparationTool
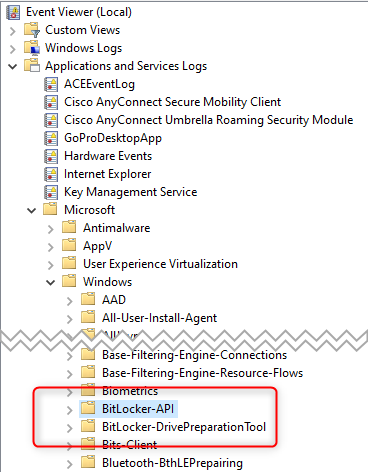
- In these logs, look for these events. Microsoft Documentation has resolutions for all these Bitlocker errors :
- Event ID 853: Error: A compatible Trusted Platform Module (TPM) Security Device cannot be found on this computer
- Event ID 853: Error: BitLocker Drive Encryption detected bootable media (CD or DVD) in the computer
- Event ID 854: WinRE is not configured
- Event ID 851: Contact manufacturer for BIOS upgrade
- Error message: The UEFI variable ‘SecureBoot’ could not be read
- Event ID 846, 778, and 851: Error 0x80072f9a
- Error message: Conflicting Group Policy settings for recovery options on operating system drives
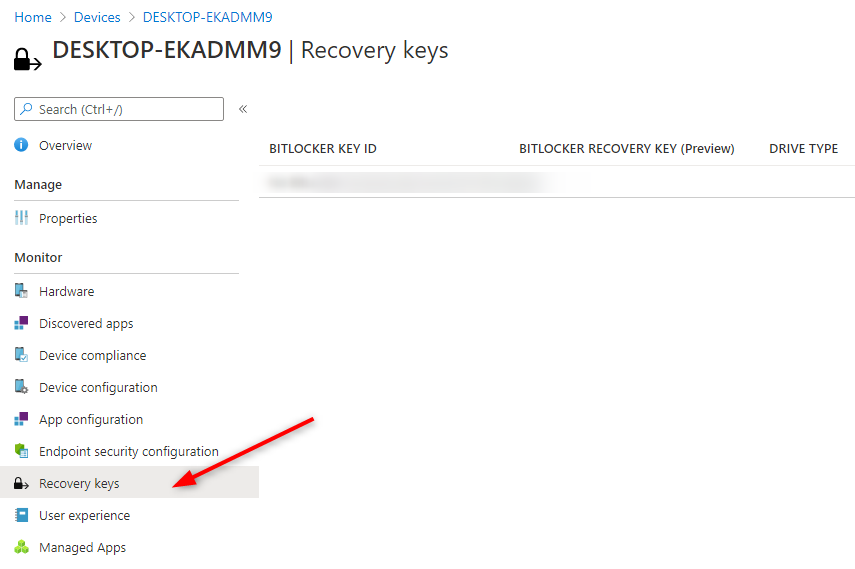
Bitlocker AAD Recovery keys
From the Intune portal, you can view BitLocker Key IDs and Bitlocker recovery keys for your Windows 10 devices
- In the Endpoint Manager Portal
- Go to Devices / All devices
- Select a device and then Recovery keys
We hope this article helps you to manage Windows 10 and your Intune Bitlocker Policy. Feel free to use the comment section if you have any questions.












Only authorized users can leave comments
Log In