
I recently found in our infrastructure that a lot of new Windows Server 2012 Core Edition were installed for specific reason. This edition can cause some problems to administrators that are not aware of SCCM commands.
Here is the list of actions that will be covered in this post:
- Configuration Manager client services and properties
- Configuration Manager agent scan trigger
- EndPoint Protection client installation and properties
- Logs directory
There’s a lot of commands that can be execute but I will give you the minimum to remember.
From ‘cmd’, type those commands for configuration manager.
| Configuration Manager | Command |
|---|---|
| Properties | control smscfgrc |
| Software Center | c:\windows\ccm\scclient.exe |
| Client Health Evaluation | c:\windows\ccm\ccmeval.exe |
| Service Start | c:\windows\ccm\ccmexec.exe |
| Service Repair | c:\windows\ccm\ccmrepair.exe |
| Service Restart | c:\windows\ccm\ccmrestart.exe |
Configuration Manager Client Scan Trigger with WMI
You can also trigger agent from WMI command line if you don’t want to open the configuration manager properties.
| Client Agent | WMI Command |
|---|---|
| Application Deployment Evaluation Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000121}" /NOINTERACTIVE |
| Discovery Data Collection Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000003}" /NOINTERACTIVE |
| File Collection Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000010}" /NOINTERACTIVE |
| Hardware Inventory Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000001}" /NOINTERACTIVE |
| Machine Policy Retrieval Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000021}" /NOINTERACTIVE |
| Machine Policy Evaluation Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000022}" /NOINTERACTIVE |
| Software Inventory Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000002}" /NOINTERACTIVE |
| Software Metering Usage Report Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000031}" /NOINTERACTIVE |
| Software Updates Assignments Evaluation Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000108}" /NOINTERACTIVE |
| Software Update Scan Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000113}" /NOINTERACTIVE |
| State Message Refresh | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000111}" /NOINTERACTIVE |
| User Policy Retrieval Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000026}" /NOINTERACTIVE |
| User Policy Evaluation Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000027}" /NOINTERACTIVE |
| Windows Installers Source List Update Cycle | WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000032}" /NOINTERACTIVE |
Troubleshooting
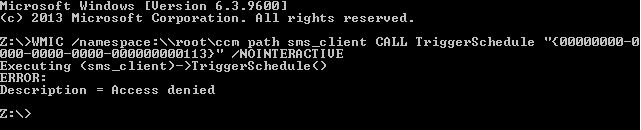
Make sure to run those commands as administrator else you will receive an access denied error message.
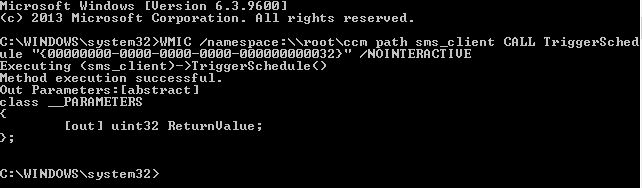
If the execution is successful, you should see something like this.
Configuration Manager Client Scan Trigger with Powershell
*** Update : 2014-10-30 *** Thanks to MaxFlipz for this addition.
Powershell can also be used to launch scans on clients whether local or remote. Simply use the command Invoke-WMIMethod:
$Server = Server Name where you want to run the trigger. You can remove -ComputerName if you are locally on the server.
| Client Agent | Powershell Command |
|---|---|
| Application Deployment Evaluation Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000121}" |
| Discovery Data Collection Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000003}" |
| File Collection Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000010}" |
| Hardware Inventory Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000001}" |
| Machine Policy Retrieval Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000021}" |
| Machine Policy Evaluation Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000022}" |
| Software Inventory Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000002}" |
| Software Metering Usage Report Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000031}" |
| Software Update Deployment Evaluation Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000114}" |
| Software Update Scan Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000113}" |
| State Message Refresh | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000111}" |
| User Policy Retrieval Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000026}" |
| User Policy Evaluation Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000027}" |
| Windows Installers Source List Update Cycle | Invoke-WMIMethod -ComputerName $Server -Namespace root\ccm -Class SMS_CLIENT -Name TriggerSchedule "{00000000-0000-0000-0000-000000000032}" |
Endpoint Protection Client Installation and Properties
*** Update : 2015-05-08 ***
You can install an EndPoint Protection client locally on a machine with FEPInstall.exe. Simply copy the file somewhere locally on the device and execute with an elevated command prompt.
| Client Installation | FEPInstall Switches |
|---|---|
| Silent setup | /s |
| Silent extraction of the setup files | /q |
| Normal installation | /i |
| Install without uninstalling third-party software | /noreplace |
| Policy file to be used to configure the client software | /policy |
| Client software installation is opted in to the Microsoft Customer Experience Improvement Program. | /sqmoptin |
You can refer to TechNet for more details about FEPInstall.
You can manage a local EndPoint Protection client with MpCmdRun.exe. This table shows switches that can be used with the command line.
| Client Action | MpCmdRun Switches | Additional Switches |
|---|---|---|
| Scan for malicious software based on default configuration | -Scan -ScanType 0 | |
| Quick scan for malicious software | -Scan -ScanType 1 | |
| Full system scan for malicious software | -Scan -ScanType 2 | |
| File and directory custom scan for malicious software | -Scan -ScanType 3 | -File -DisableRemediation -BootSectorScan -Timeout |
| Begins tracing Microsoft antimalware service's actions | -Trace | -Grouping -Level |
| Gathers a bunch of files and packages them together in a compressed file in the support directory | -GetFiles | -Scan |
| Restores the last set of signature definitions | -RemoveDefinitions -All | |
| Remove all Dynamic Signatures | -RemoveDefinitions -DynamicSignatures | |
| Performs definition updates directly from UNC path file share specified | -SignatureUpdate -UNC | -Path |
| Performs definition updates directly from Microsoft Malware Protection Center | -SignatureUpdate -MMPC | |
| List all quarantined items | -Restore -ListAll | |
| Restores the most recently quarantined item based on threat name | -Restore -Name | -Path |
| Restores all the quarantined items | -Restore -All | -Path |
| Adds a Dynamic Signature | -AddDynamicSignature | -Path |
| Lists SignatureSet ID's of all Dynamic Signatures | -ListAllDynamicSignatures | |
| Removes a dynamic signature | -RemoveDynamicSignature -SignatureSetID | |
| Enables integrity services | -EnableIntegrityServices | |
| Submit all sample requests | -SubmitSamples | |
Use MpCmdRun alone to see additional information about the switches.
You will receive a return code if you use switch -Scan.
- 0 if no malware is found or successfully remediated
- 2 if malware is found and not remediated
Logs
You can find configuration manager logs in C:\Windows\CCM\Logs for any troubleshoot or C:\Windows\CCMSetup for installation logs.
You are now ready to troubleshoot client on a Windows Server 2012 Core Edition.












Gold.Chapman
03.01.2020 AT 06:48 AMManoj Jain
02.10.2020 AT 04:08 PMGuenay
01.17.2020 AT 04:41 AMHolly Newman
10.07.2019 AT 02:59 PM2XXUW3Q1 www.yandex.ru
08.29.2019 AT 05:17 PMTobbi
03.22.2019 AT 05:10 AMJoe Ismail
03.12.2019 AT 06:37 AMFiras
01.24.2019 AT 06:00 AMCS
11.16.2018 AT 09:53 AMJI
12.21.2018 AT 01:13 PMRick
10.18.2018 AT 04:04 PMRuss
05.04.2018 AT 11:00 AMSerg
07.10.2017 AT 07:17 AMBen
10.06.2016 AT 08:45 AMBrecht Gijbels
05.18.2016 AT 07:26 AMJohn
04.05.2016 AT 06:14 AMBenoit Lecours
04.06.2016 AT 11:29 AMLee Langley
04.05.2016 AT 06:18 AMRyan Steele
12.07.2015 AT 02:59 PMNicolas Pilon
12.08.2015 AT 08:19 AMkevin
12.03.2015 AT 08:26 PMNicolas Pilon
12.04.2015 AT 12:10 PMKevin
12.05.2015 AT 09:24 PM