
Microsoft has been releasing Security baseline since the Windows XP days. Windows 10 is no exception to this, except now there’s a new release of security baseline following each major build of Windows 10. The concept of the Security Baseline is to provide Microsoft guidance for IT administrators on how to secure the operating system, by using GPOs, in the following areas :
- Computer security
- User security
- Internet Explorer
- BitLocker
- Credential Guard
- Windows Defender Antivirus
- Domain Security
Implementing the security baseline in GPOs is not a complex or long task. The challenge that the security baseline provide is that it will expose areas of the environment that are not secure.
This means that to follow all Microsoft security guidelines, it would be required to fix many other systems outside of Windows 10 to achieve this.
In this post, we will describe what is the Security baseline, how to use them and key points that will most likely be challenging for other systems in the environment
Prerequisites
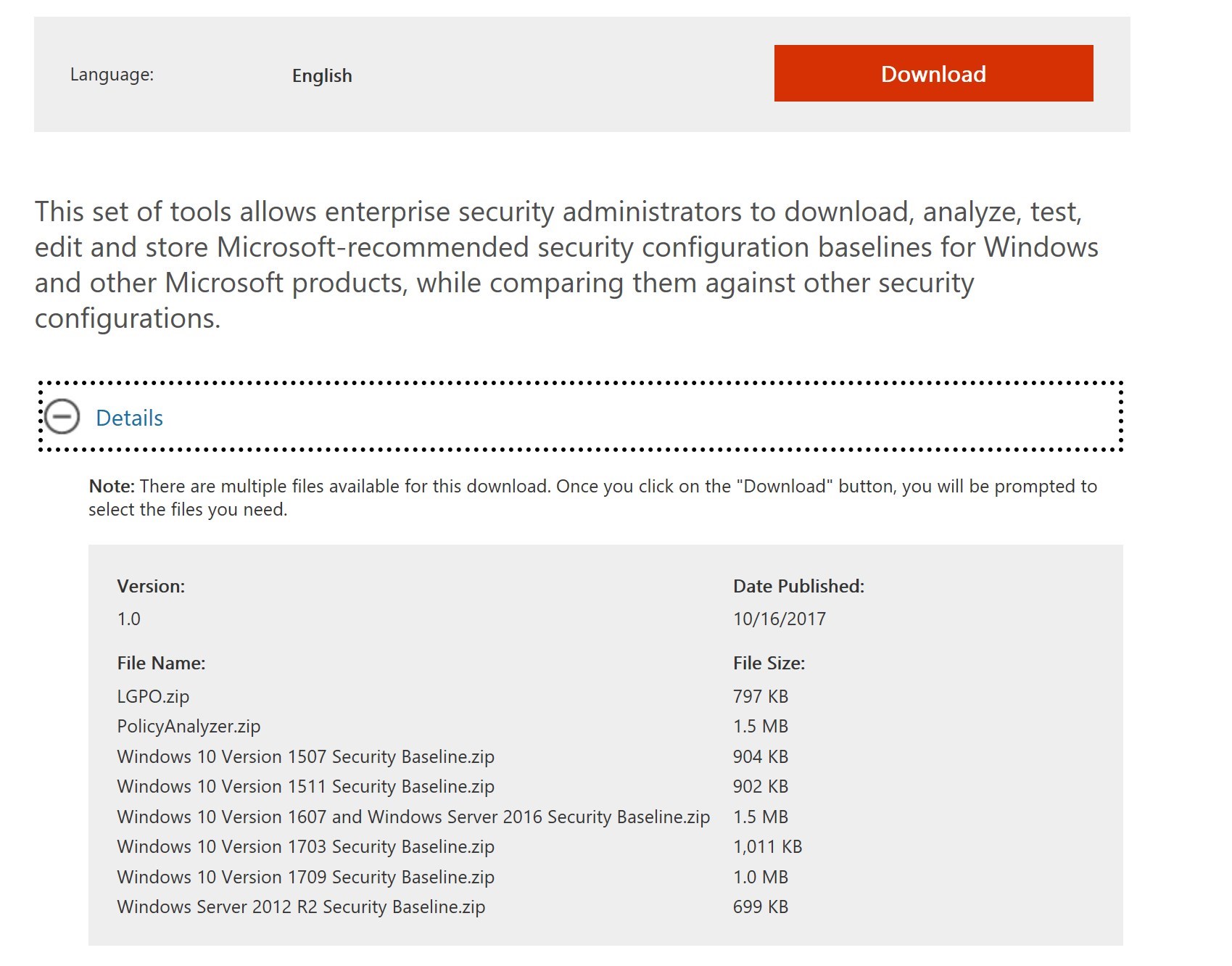
- Download the Security Baseline zip file that matches the Windows 10 version
- A new version is released for each Windows 10 major build. First in draft and then for production, in the same link
- Baselines are backward compatible, newer version provides mostly new GPOs to support Windows 10 newest features
- Security access for Group Policy Management
Windows 10 Security Baseline Files
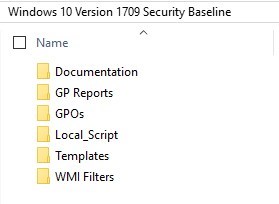
- The downloaded zip file contains all the required bits to help implement the baseline in your environment.
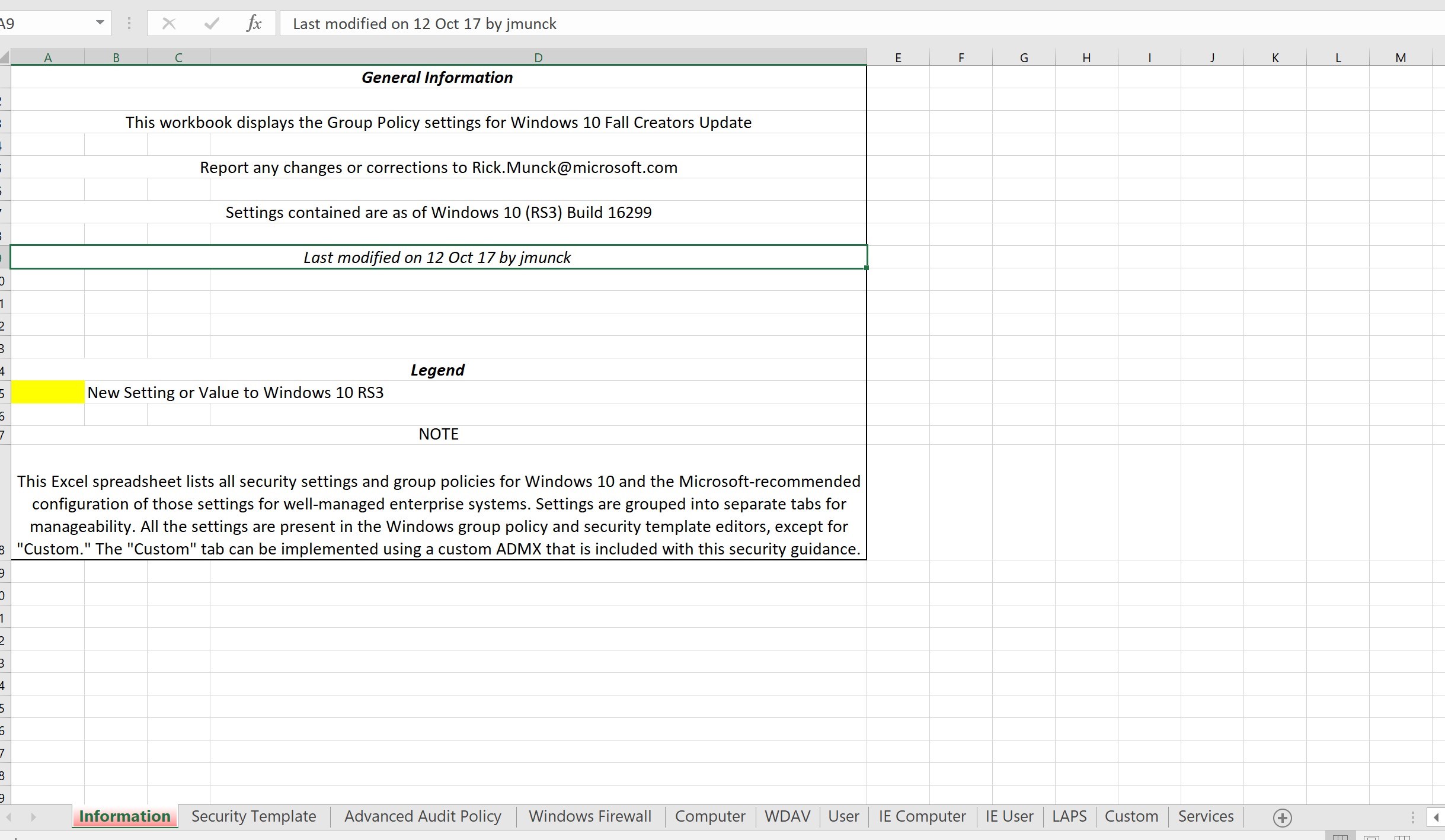
- Documentation folder contains a large Excel file with all the details of every configuration part of the baseline
- GP Reports folder contains HTML report of GPO templates available as part of the Windows 10 Security Baseline
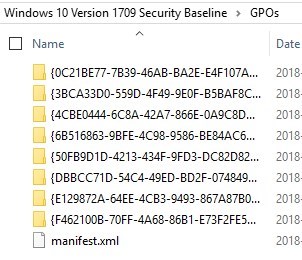
- GPOs folder contain the actual GPO files that can be imported in the Group Policy Management console
- Local_Script folder contains a script to install the security baseline into the local policy for Windows 10
- this is more for testing the actual configuration
- Templates contain ADML and ADMX files for additional settings in the GPOs
- WMI Filters folder contains two WMI filters: Windows 10 and Internet Explorer 11
How to use Windows 10 Security Baseline
Add Templates to Central Store
- Copy the ADMX from the Templates to the GPO Central Store
- Copy the ADML from the templates to the GPO Central Store EN-US subfolder
If you are not familiar with the Central Store for GPO, please see Microsoft documentation
Import GPOs
- Create a new blank GPO
- Right-click on the GPO, and select Import Settings
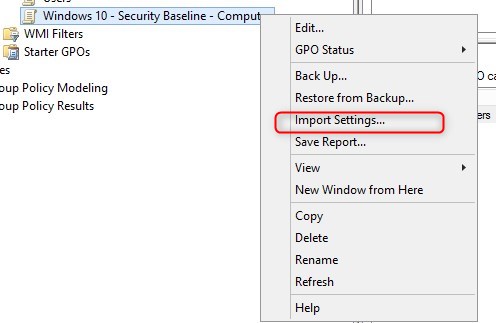
- Click Next
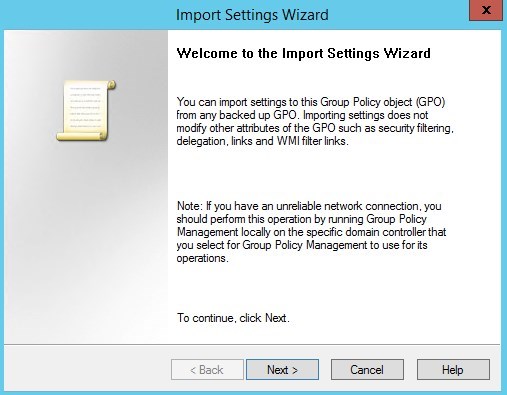
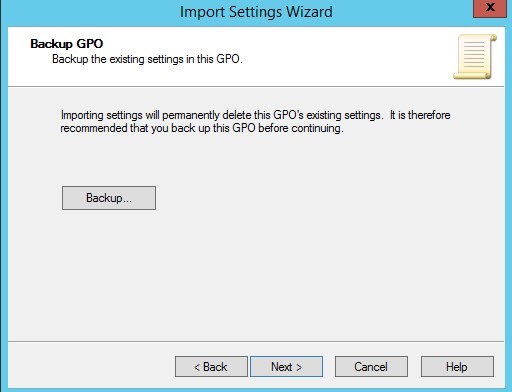
- Click Next, no need to take a backup of a new blank GPO.
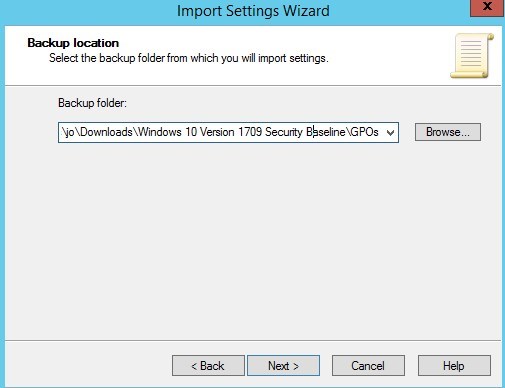
- Browse to the GPOs folder and click Next
- Select the GPO to be imported, based on the name and click Next
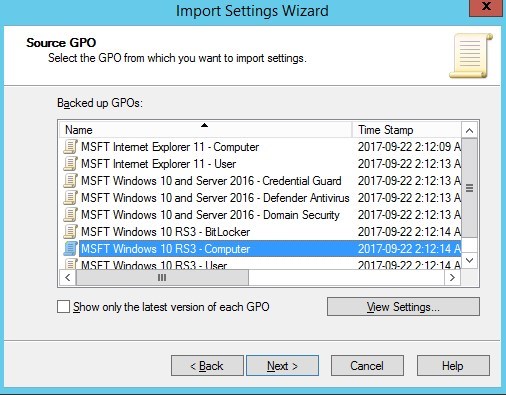
- Click Next
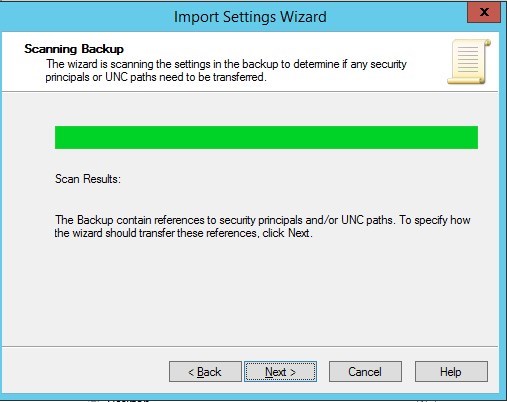
- Select Copying them identically from the source and click next
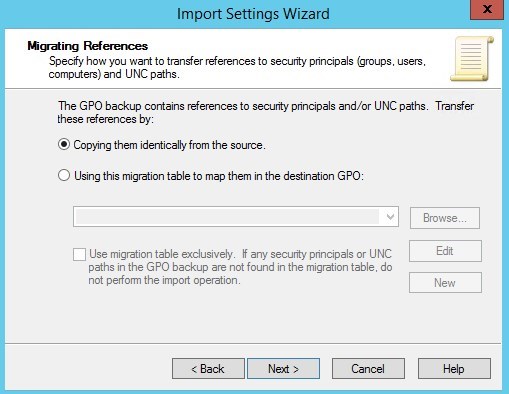
- Click Finish
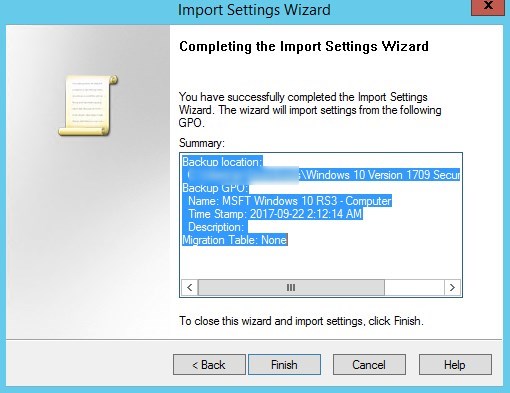
- Click the Settings tab to see all the configuration imported
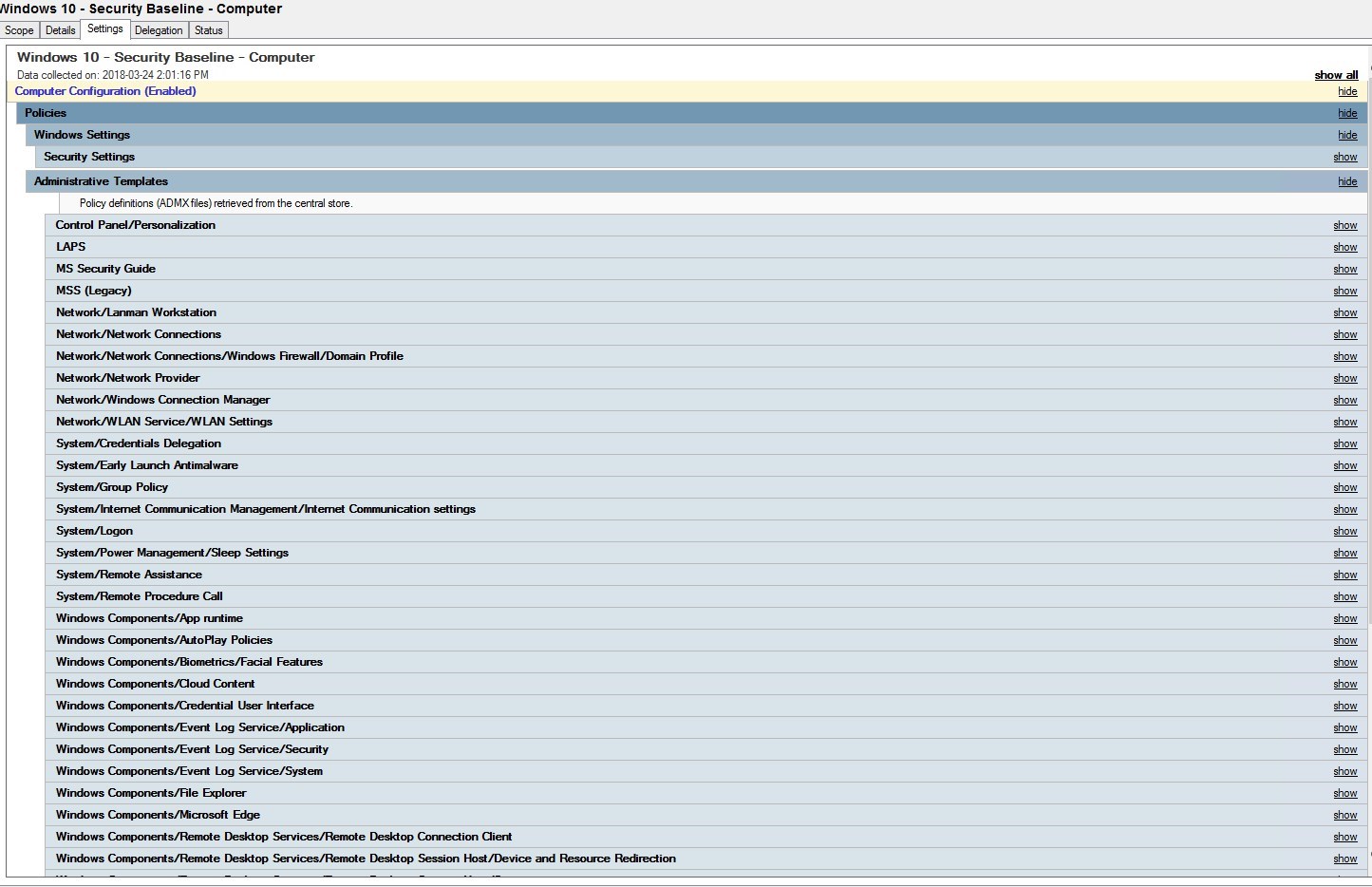
Once the GPOs are imported, testing is key!
No magic trick here, start with test computers and then IT users/pilot users prior to applying this to production.
Key points that provide challenges
Here are some configurations that are part of the baseline that should be looked at up front as they might provide issues with your environment. The idea here is to have a better understanding of what is going on. Don’t go and change those settings to avoid issues. The issues should be fixed at the other end for better security.
Hardened UNC path
This setting is likely to give the following error when trying to process GPO on Windows 10.
The processing of Group Policy failed. Windows attempted to read the file \\yourdomain.fqdn\sysvol\yourdomain.fqdn\Policies\{GPO GUID}\gpt.ini from a domain controller and was not successful.
The configuration Computer/Administrative Template/Network/Network Provider/Hardened UNC Path
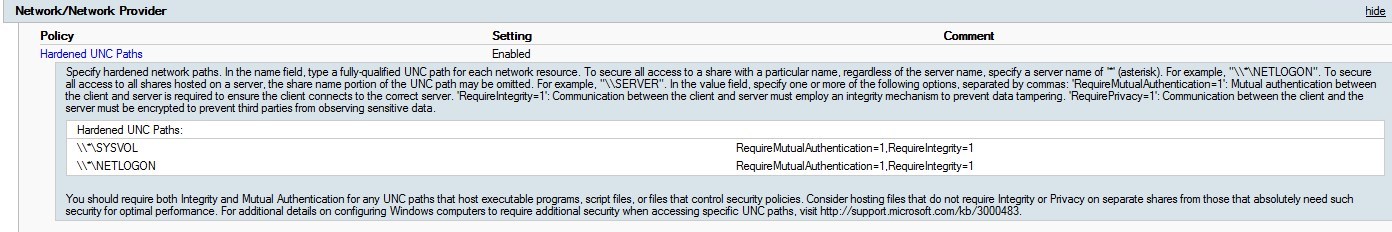
Review the following post by Lee Stevens for details on the UNC hardening path to help define this setting for your environment
Internet Explorer process only computer GPO
If you have user GPO for Internet Explorer, in the Security Zone, adding the baseline for Internet Explorer will prevent those settings to be applied.
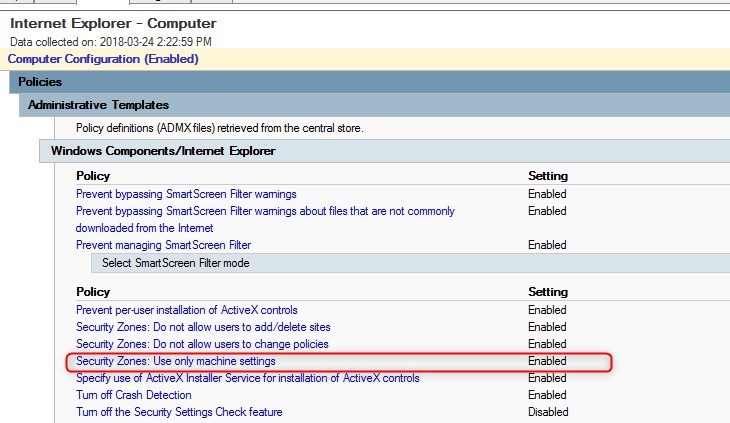
Two options are available if this causes issue:
- Move your Internet Explorer configuration to computer GPO instead of user GPO
- Change the configuration back to Not Configured for this GPO
More details on this KB from Microsoft
User Account Control
The user account control (UAC) is configured to the maximum level with the Security Baseline.
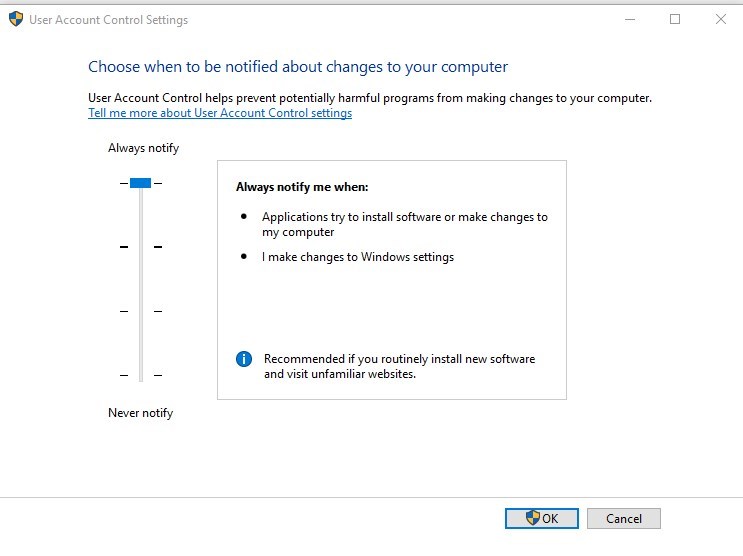
The default Windows 10 level is set to Notify me only when applications try to make changes to my computer (level 3 out of 4)
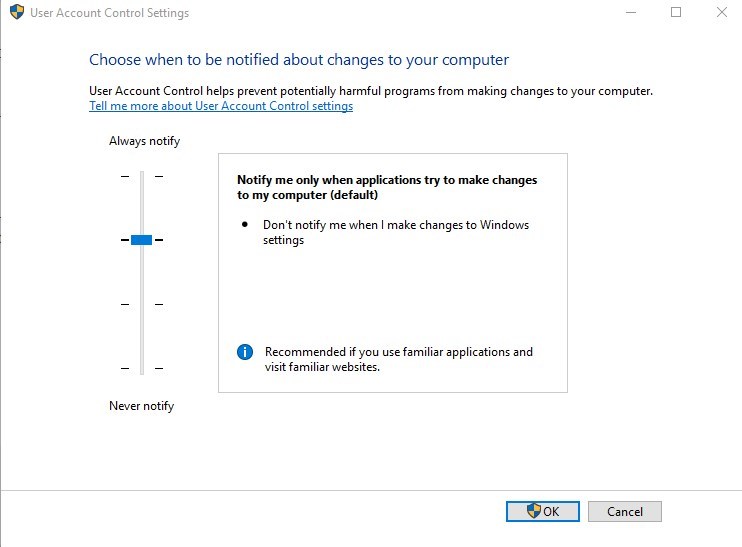
This is configured by a local security policy
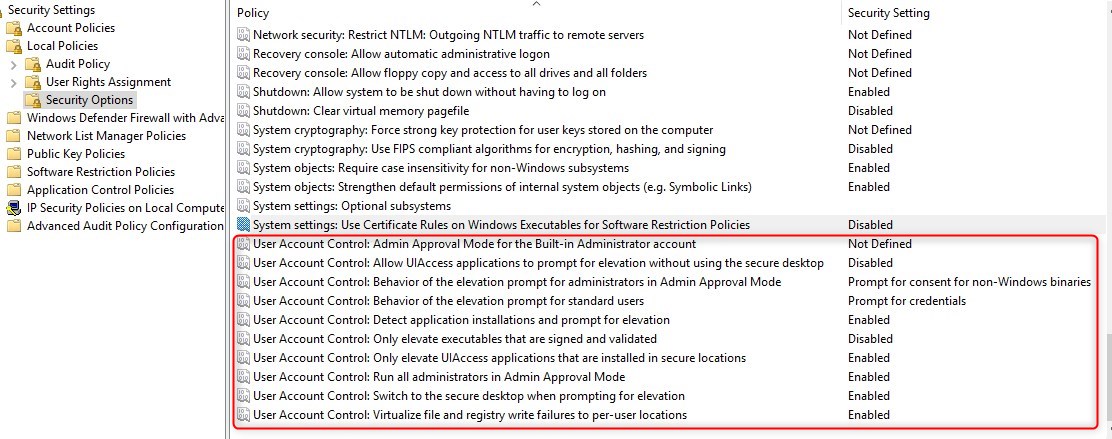
To modify the GPO, under the Windows 10 Computer GPO Computer/Windows Settings/Security Settings/Local Policies/Security Options/User Account Control
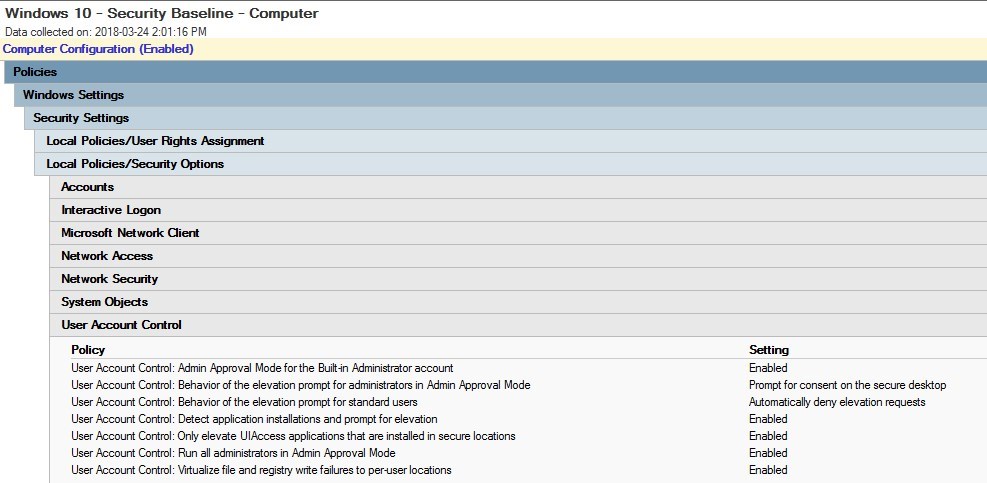
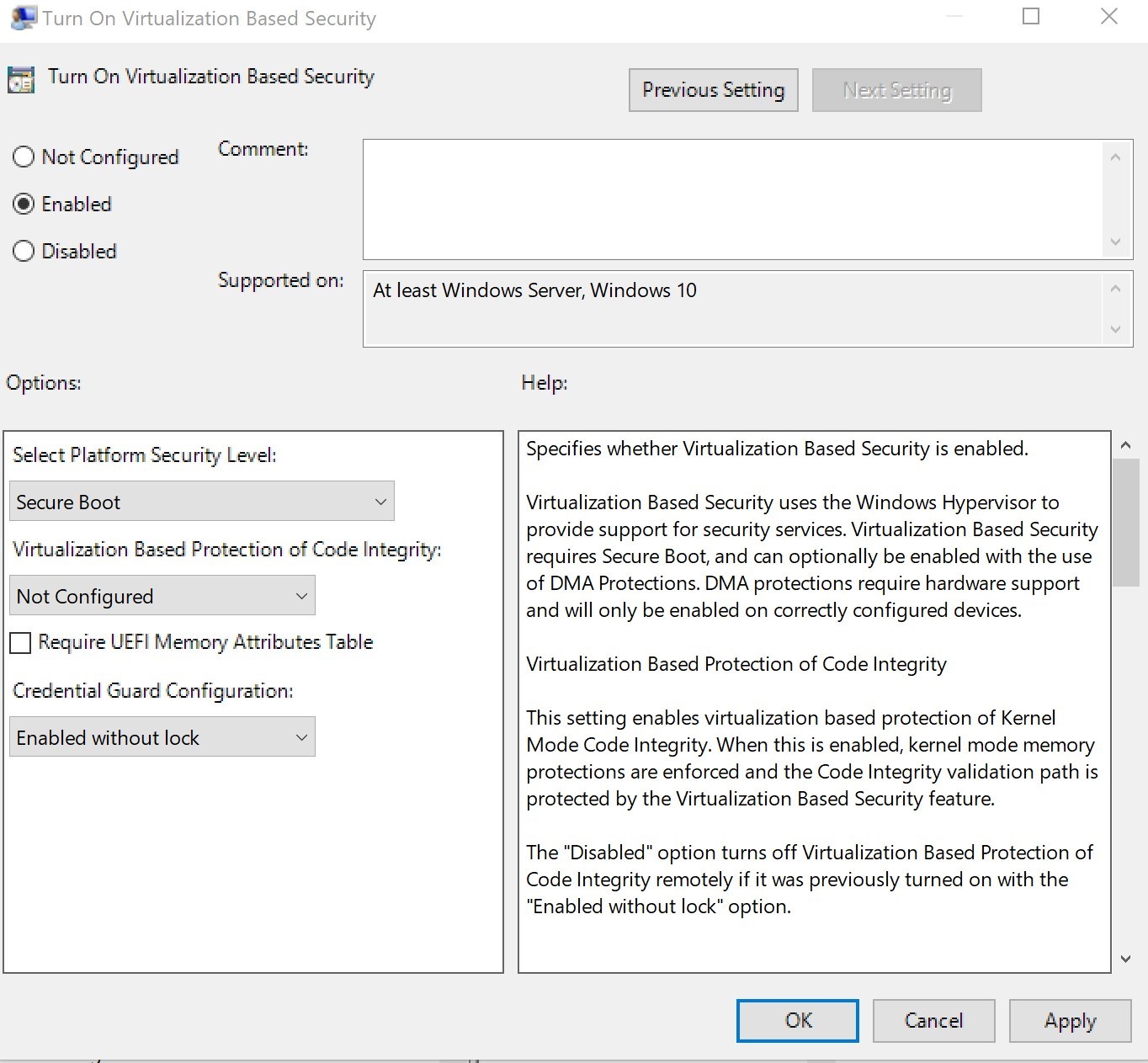
Credential guard
Having Credential guard in Windows 10 is categorized as a quick win solution as the requirement and setup is easy.
The default configuration as part of MSFT Windows 10 and Server 2016 – Credential Guard GPO is configured in a way that is likely to crash the computer or have an undesired requirement for future needs if applied as is.
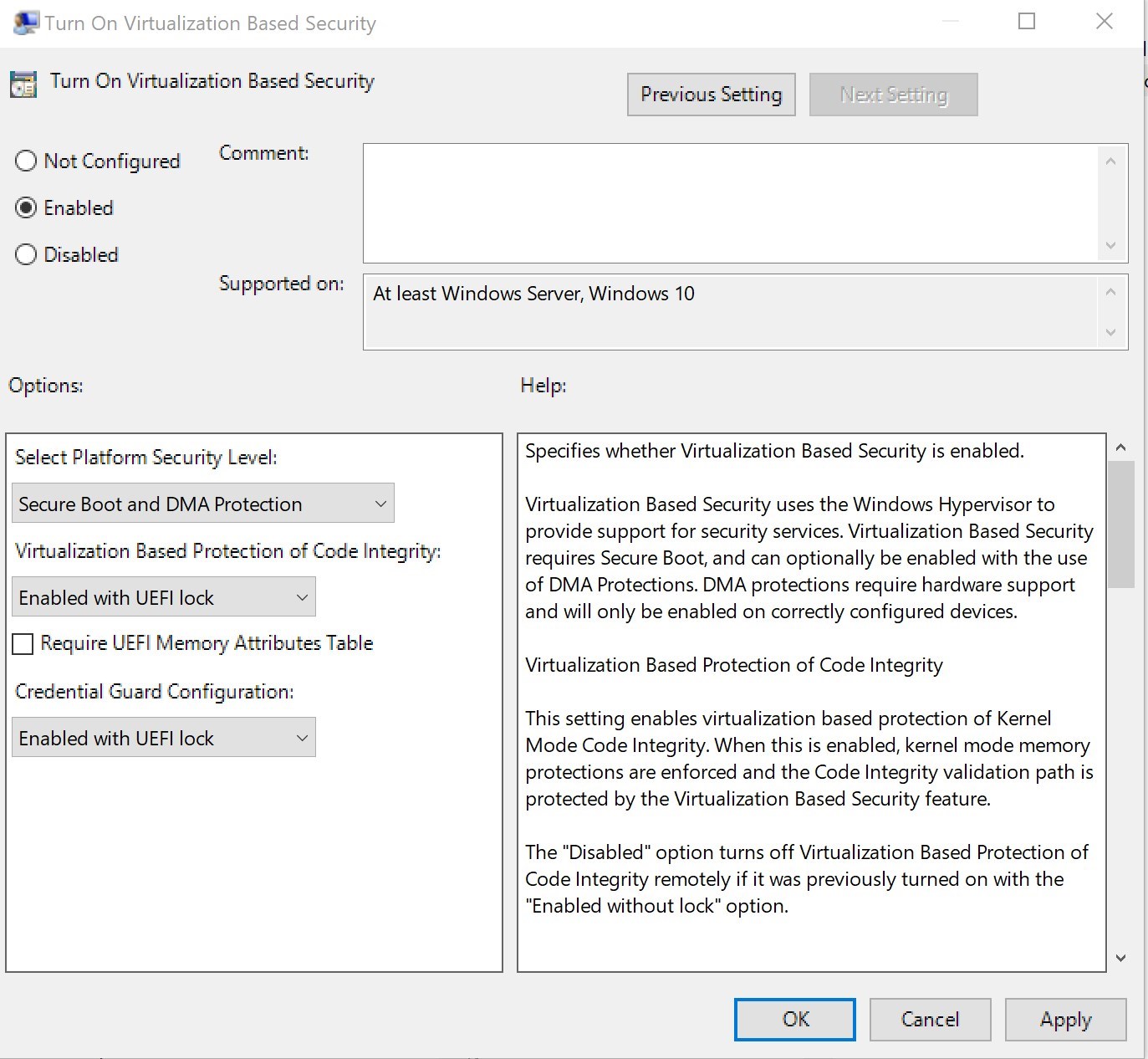
We strongly recommend to carefully read the Help section of the Computer/Administrative Templates/System/Device Guard/Turn On Virtualization based security GPO
To take advantage of Credential Guard safely, this would be the required configuration.
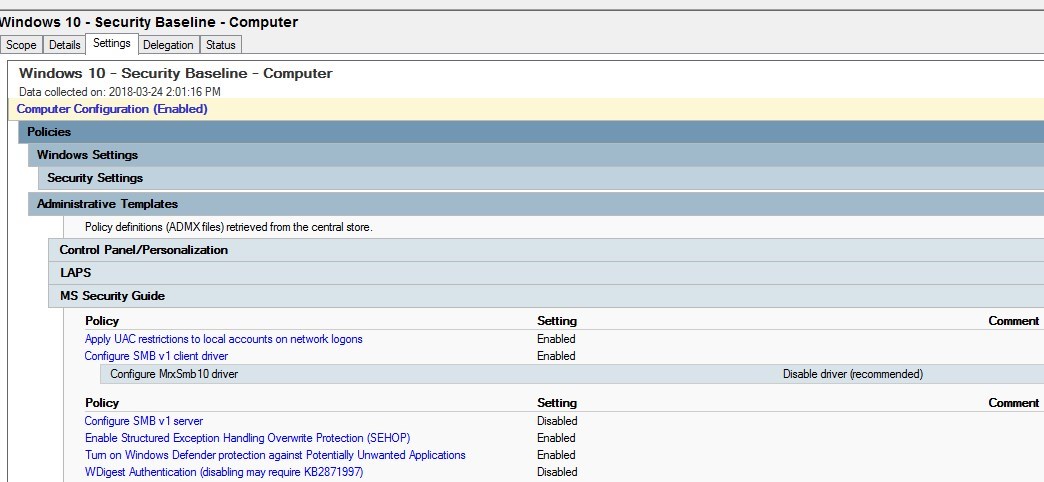
SMB v1
This topic is the most important of all key points. With Windows 10 v1709, SMB v1 is disabled by default. But what if you still need this in your environment?
Let me make this clear, we do not recommend enabling SMB v1. It has been proven to be one of the most critical security hole as of late with malware like WannaCry.
On the other hand, sometimes we don’t have much choice to go against security.
So to leave SMB v1 enabled as part of the security baseline GPO, we suggest reading the following blog post by Aaron Margosis
The GPO settings for SMB v1 are under Computer/Administrative Templates/MS Security Guide
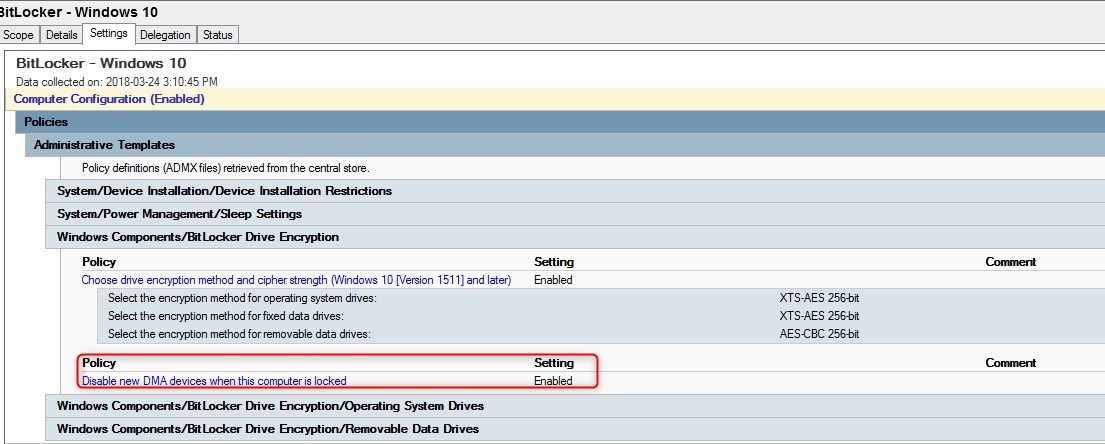
Issue with BitLocker on Windows 10 1709
The MSFT Windows 10 RS3 – BitLocker GPO contains a setting to Disable new DMA devices, that broke some computer.
See the following blog post by Aaron Margosis for details on the issue.
The setting Computer/Administrative Templates/Windows Components/BitLocker Drive Encryption/Disable new DMA devices when this computer is locked, should be reviewed prior to being applied.
What to do when a new version of Security baseline is available?
A new version of Security baseline usually come out at the same time as a Windows 10 build goes RTM.
Microsoft has always released them as a DRAFT version that goes on for a couple months and then release the FINAL version.
Here’s a checklist for what to do when the new version is available :
- Start by reviewing the Excel file to see what’s new to the baseline
- Most of the new settings in the baseline will be in line with new features as part of the Windows 10 release
- Update ADMX in the Central store with the ones from the latest Windows 10 build prior to adding new settings
- New settings should then be added to your environment by one of the following :
- Import the new GPOs
- Add new settings to current GPO
Follow us on Twitter to get a notification when a new version of the Security baseline is released.
Bonus Tip
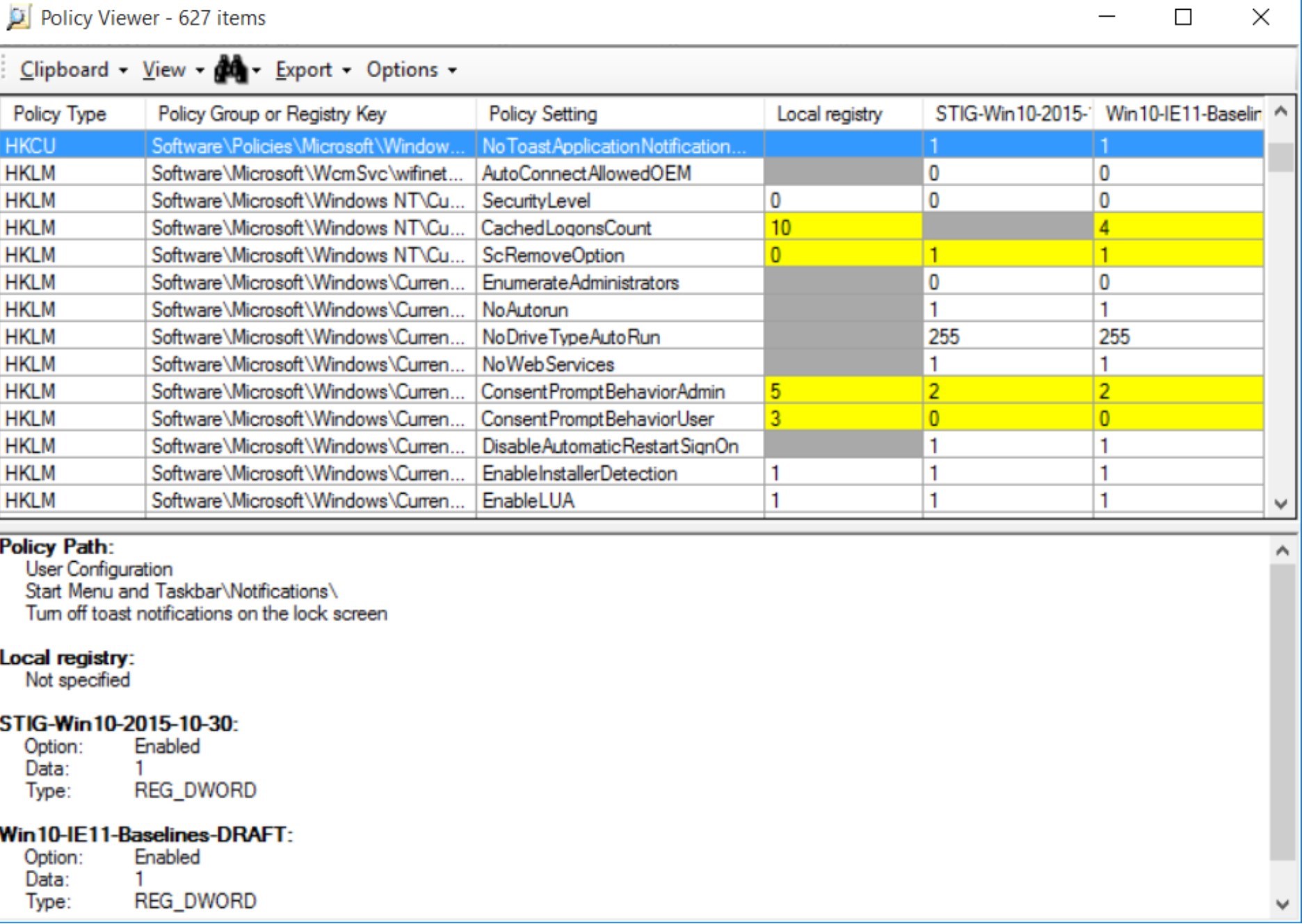
The Policy Analyzer is a great tool to compare current GPOs against the ones from the Security Baseline.
This can give an idea of the conflicting settings as well as additional settings from the Security Baseline











Shall remain nameless
11.05.2019 AT 03:09 AMRobert Manahan
07.17.2019 AT 11:22 AMpanda support
08.20.2018 AT 03:08 PMrasheedah muhammad
06.06.2018 AT 08:39 AMJesus Gonzalez
04.23.2018 AT 11:36 AMAndrew
03.29.2018 AT 03:57 AMMark Payne
03.27.2018 AT 10:51 AMQuinn
03.26.2018 AT 10:27 PMJonathan Lefebvre
03.27.2018 AT 08:00 AM